隐秘的角落
加密后的数据在init函数有异或0x23的操作,是rc4加密
1 | import base64 |
得到56e83694-f976-11eb-b343-faffc201c8e0
再md5加密小写就是flag
ezGo
go题一些陌生的函数以及奇怪的变量配合动调体验更加
这里的循环的作用主要是把输入的40个字符的ASCII码拼接成一个大整数
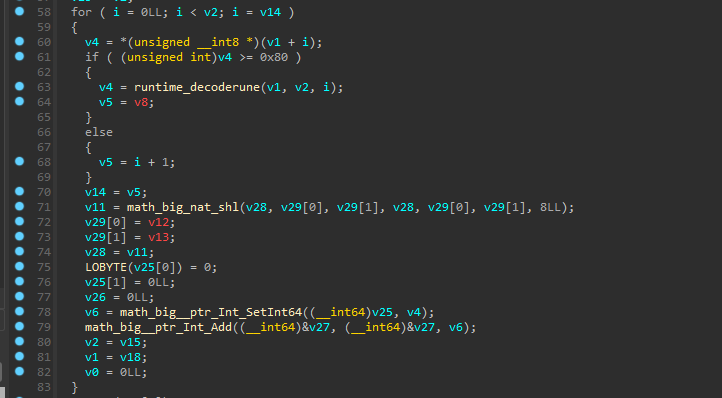
然后就是平方取余比较
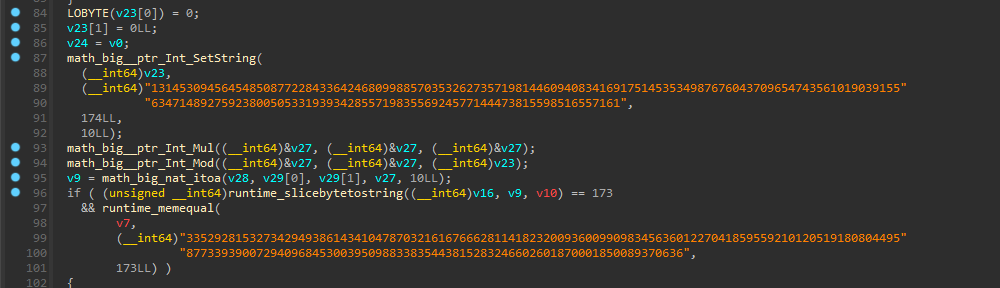
加密就是如下
$$
c=m^2modn
$$
一种特殊的RSA加密形式,用rabnin算法解

用yafu分解大质数,可以发现这两个质数都是模四余三,根据e=2可知,这是一个rabin算法。
1 | import libnum |
得到flag:DASCTF{48fa8aa2b489e9adac1750ea16ddc7b5}
fantansic maze
- sha256爆破
- 自动化路径求解
- bfs算法
首先是常规的sha256爆破
过了proof之后题目会给出远程程序的base64编码,将编码解码后写入文本再拖入IDA查看
其中有1000个相似的函数,其汇编代码大致如下(这里IDA F5看不出来啥东西)
1 | .text:0000000000001358 function_0 proc near ; CODE XREF: function_36+85↓p |
转换为伪代码大致如下
1 | tmp++; |
从function_0 ~ function_999都能跳转到其它的十个函数,我们的目标是要在第1000步的时候走到function_1000从而获得flag
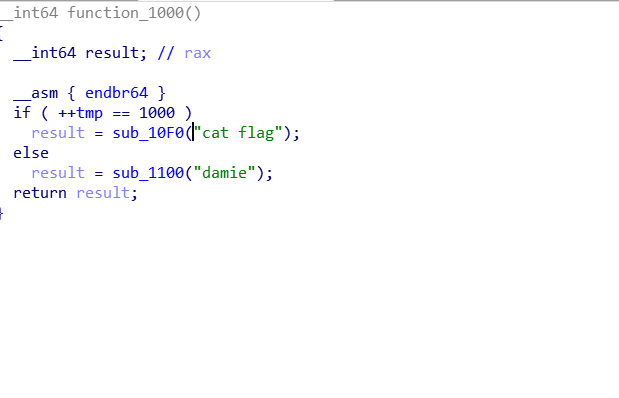
但是这里可以发现在每一个switch内只要default就会返回main函数,那么我们其实只需要找到一条长度小于1000的路径,然后一直default去填充tmp就好了
寻找最短路径可以采用bfs算法,那我们只需要知道1000个函数每个函数可以跳转到那些函数就好了,但是由于每一次的maze都是随机生成的且超过20秒就会直接Alarm clock,所以我们不能通过IDA来直观的得知程序的构造,而是需要我们手动分析hex view来得到程序的构造
分析Hex View主要分析的就是call指令
call指令占5个字节,如00000000000013BF call function_541 在 Hex View 中为\x00\x01\xbd\x7b\xe8(这里为大端序), \xe8可以理解为标志位,\x00\x01\xbd\x7b为地址到跳转函数的00000000000013BF偏移,而这里每一个函数的偏移为0xd3,这里就可以通过偏移来算出call指令所指向的函数
这里得注意下这里得偏移是有符号数,所以在计算的时候需要将其转换
最后,在得到表之后,用bfs算法得到路径,最后得到flag
1 | #!/usr/bin/python3 |